We already discussed passwords in the previous issue of the Bulletin. However, as many of you figured out, that was just an April Fools’ hoax and all those considerations are void. Apologies to those who felt confused… Hence, let’s get serious again.
There are many ways to lose your password. By handing it out involuntarily when you fail to spot a phishing attack against you. By having your home PC, laptop or smartphone infected with some malware that steals your password directly when you type it in. Or when the password database used by your favourite cloud service provider is hacked. But unless the attackers abuse your password – and with it the access to your computing account – in a very visible way, how would you know?
Of course, it’s easy to spot if your password has been used to send spam into the world (resulting in your mailbox overflowing with thousands of [out-of-office | non-delivery | angry] replies), to place orders on your behalf (and all your money is gone), to post offensive or nasty messages in your Instagram timeline, Twitter tweets or chat group (and you receive a backlash in return), to log in from far away (and you get a warning), or to compromise your laptop (and end up with all your data encrypted by ransomware). But what if that’s not the case? What if the attackers just sit tight and keep your password as a trophy, a token, an opportunity to be used later? Or a commodity to be sold on the dark web to attackers who do want to strike?
The first stop depends on your personal vigilance. Monitoring your devices for any weird activity, installed programs or behaviour. And monitoring your logins! CERN – like Amazon, Google and many others – monitors your login activity and notifies you in case your most recent login is “bizarre”, like a login from Melbourne when you live in Paris, from Amsterdam when you study at UCLA, or from Hong Kong when you work in Buenos Aires.
A second-stop shop to learn whether your password has been compromised in the past is the website “have i been pwned?”. While it might be counterintuitive to enter your email address into an unsolicited site like this, the reputation and integrity of its maintainer, security expert Troy Hunt (find his presentation at CERN here: https://cds.cern.ch/record/2693939), guarantees its trustworthiness.
The password database of Troy Hunt is only one of many. Via our network of peers and friends, through protective intelligence and from other publications, the CERN Computer Security team has been able (and continues) to gather zillions of tuples of {email address/account name and password}. In rare cases these tuples even list the origin of the password exposure. And these tuples are actionable. If it’s a valid CERN computing account, the action is simple: you’re asked to check all your devices for any sign of compromise and you’re forced to change your CERN password the next time you log in1. Alternatively, if the email address is registered with CERN2 but used with an external cloud service (Amazon, Twitter, YouPorn, you name it…), the corresponding owner will receive a notification including the partially obfuscated clear-text password (given that it has already been exposed, the password is “burned” in any case!). The notification also indicates where the password has been used, if known (and, no, if it’s not indicated, we really don’t know either, so please don’t ask).
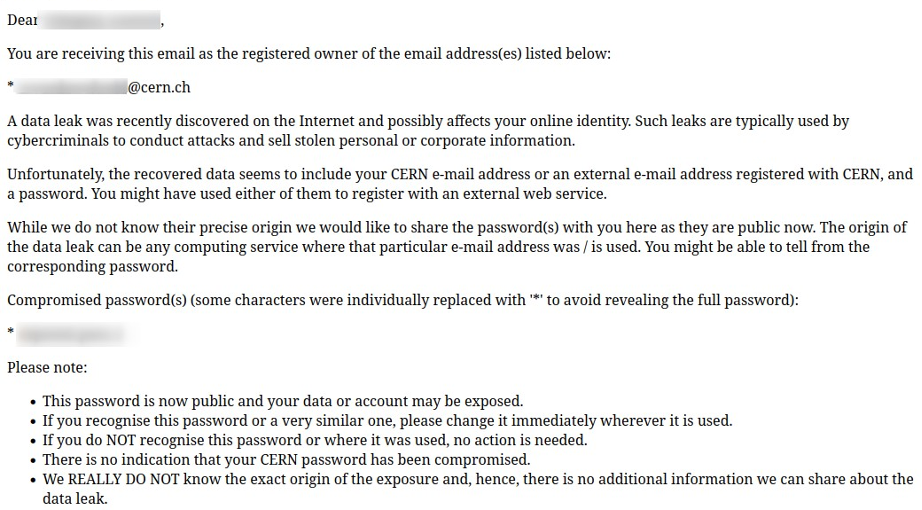
As the aforementioned “zillions of tuples” also contain information on other institutes and universities, international organisations and agencies, partners and peers of the CERN Computer Security team, aggregated notifications are also sent to the corresponding Computer Security Incident Response Teams (CSIRT) of those entities, so that they can follow up directly with their users. Every single password change counts. Every re-protected account counts. The fewer remain compromised, the better for the security posture of us all.
So, unless you employ the ultimate silver bullet to protect your account and greatly reduce the consequences of a compromised password, namely two-factor authentication3, watch out! Is this password yours?
______
Do you want to learn more about computer security incidents and issues at CERN? Follow our Monthly Report. For further information, questions or help, check our website or contact us at Computer.Security@cern.ch.
1: In the past, the annual password change was another catch-all, but as it happened annually, the time between the password being compromised and action being taken could have been a whole year. Reducing the frequency of resets improves on that, but also results in weaker passwords as people have to invent new passwords every n months. That’s why CERN decided to give up on password resets and concentrate instead on password disclosure databases (https://home.cern/news/news/computing/computer-security-password-revolutions).
2: These are not necessarily only @cern.ch email addresses, but also external email addresses used as aliases, forwarding destinations, back-ups or those registered with a home institute or university.
3: While stealing your password might have been “easy”, getting hold of your smartphone or login dongle is hard.
